So Industry 4.0 is here to stay
IIoT has already transformed manufacturing. There’s no turning back. Manufacturers, especially discrete manufactures, can no longer afford to ignore it, nor can they stick with traditional processes. Why? Because they will not survive the fierce competition of the age of Industry 4.0, or the digital connected factory, if you wish to use simpler words.
IIoT offers discrete manufacturers clear and significant technological improvements that help them optimize their production, cut losses, minimize waste and gain a huge advantage over competitors that are not there, yet.
It means that once top tier discrete manufacturing industry way paves on-board Industry 4.0, all others must join the game or die.
And if you are not convinced yet, just see what top tier C level executives think and do about ‘Industry 4.0’, IIoT and the connected factory:
But, and that’s a big ‘but’, onboarding IIoT is not riskless.
That’s why so many manufacturers, especially in the Aerospace & Defense industry, tell us that they feel like “they are doomed if they do and doomed if they don’t”. Well there’s a solution. But first, let’s talk risks.
Cloud Security Risks in Industry 4.0
When professionals talk and think about the digital and connected factories, they almost always think about the security risks.
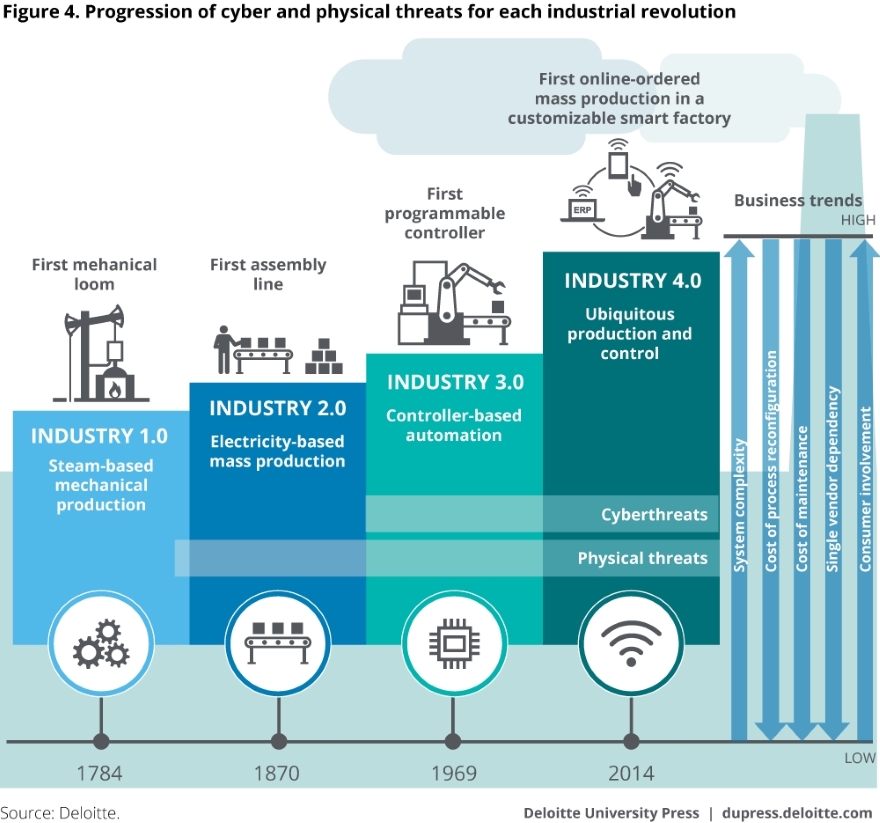
Although the industrial sector and security risks “have been related as long as production has been mechanized”, as Deloitte describe it in their paper, Industry 4.0 as a whole brings with it enormous benefits and fearful risks to the table: cybersecurity risks that are “the greatest leaps in cyber risk to date.”
Cloud security risks are not at all new, people shop, store and share valuable information, communicate with one another, make payments and bank transactions, and so forth, all in the cloud.
But when it comes to discrete manufacturing in an ‘Industry 4.0 age’, it becomes a known barrier that prevents manufacturers from adopting advanced technologies.
But putting your head in the sand won’t help in this case, and there’s no point in fearing technology to the extent that you are held back from implementing it, because, first, that will serve right to the hand of your competitors. Second, I know no past evidence of fear managing to hold technology back, no matter which field or target industry it’s related to. And last, when you decide to jump in the water you may be very late, and bare the annoying consequences that those who are late usually bare.
Since we had to learn everything there is to learn about IIoT cybersecurity, and we’ve been implementing cloud security solutions in our SAAS software, (serving discrete manufacturers that are, quite rightfully, extremely concerned about security issues, we had to become IIoT security experts). I would like to share some of that gained knowledge.
I believe that if manufacturers were to know more about the security risks and how to mitigate them, they would better understand how to leverage Industry 4.0, they will have a bigger sense of control and they will be more liberal about implementing new technologies that are here to stay anyway.
Why even be concerned?
Don’t get me wrong … the manufacturers’ hesitation is justified. It seems that cybersecurity attack attempts on IoT connections will grow, as Gartner predicts: “by 2020, more than 25 percent of identified attacks in enterprises will involve IoT.”
And when it comes to IIoT, examples of past industrial cyber attacks exist:
- The notorious Stuxnet
- The Havex
- WannaCry (Boeing was one of its victims)
- Petya
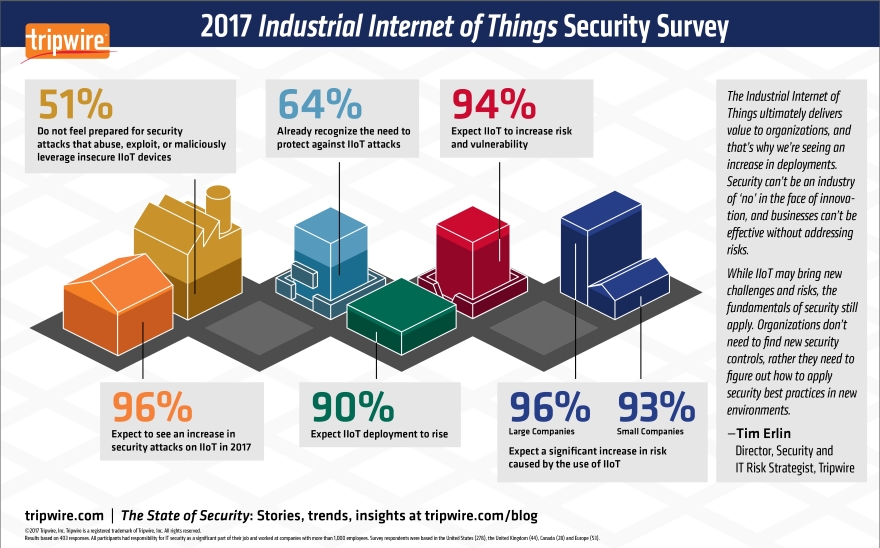
These attacks show that the industrial sector is under risk. A Tripwire Study from 2017 found that “96% of IT Security Professionals Expect an Increase in Cybersecurity Attacks on Industrial Internet of Things”.
Turning a blind eye
While many manufacturers are postponing the implementation of IIoT solutions due to raised concerns, others are jumping into the water (which is good) without taking prior precautionary steps (which is not so good). According to a Deloitte survey “Almost one-third of manufacturers have not performed any cyber risk assessments specifically focused on the ICS operating on their shop floors.
This could pose a significant risk to their operations. Nearly two-thirds of companies that have performed an ICS cyber risk assessment used internal resources, potentially introducing organizational bias into the assessment process.”
I assume that this is the result of insufficient knowledge about IIoT security risks, as well as how to successfully onboard industry 4.0 and the right steps to take to ensure safety.
What type of cloud security breaches must discrete manufacturers be aware of?
The most recognised risks are characterised by external attacks of organized groups or individual hackers: crime or politics motivated.
Indeed, this scenario is the most dramatic one. That’s why we are often exposed to it by the movie industry.
The Stuxnet worm that targeted Iran is a good example of such an external, politically motivated attack (malware), because it goes to show nobody is immune; you see, private organisations were infected as well, such as Chevron.
The ‘industrial sector Havex malware’ (a RAT (remote access trojan) that steals data from supervisory control and data acquisition (SCADA) systems or industrial control systems (ICS)) is another good example. Havex attackers used a “watering hole” technique (the terms comes from wildlife, where predators wait for an opportunity to attack their thirsty prey near watering holes) to draw victims to an infected website, to maximize the impact.
In this example, the malware could access hardware as well: “Using OPC, the malware component gathers any details about connected devices and sends them back to the [command-and-control server] for the attackers to analyze”. It was not used to control connected industrial hardware. In other words, the harm in this case was data leakage, for intelligence purposes.
If you are wondering, there are clear ways to handle these kind of threats.
Espionage in transformation of information by employees is another type of risk. Here, the source is internal. When we think of internal employees, it might seem that there’s more control and minimal risks, but since multiple IIoT systems don’t use authentication or encryption mechanisms, this might not be the case. That is why securing IIoT solutions by making sure it offers authentication or encryption is so important. Gillette incident, where an engineer spilled the beans on the company’s secret new razor design to a competitor, is a known example of industrial espionage.
Another, ‘less interesting’ format of threat is the result of simple, honest mistakes – errors (mostly by humans). Human errors, according to Chief Executives, are responsible for most (90%) cybersecurity breaches. Not something to take lightly. That’s why training employees and partners is key to cybersecurity efforts.
So, what should manufacturers do?
Like with any other form of threat, vast knowledge and proper planning can minimize or even completely eliminate risks. At the very least, they can help you minimize the pain once you’ve been attacked.
- Choose ‘the right’ IIoT partner –
Not all IIoT solutions are born equal. Not all vendors focus on the same things. If cyber security is important to you (can it not be??), make sure the IIoT solutions that you choose to implement are well prepared for security vulnerabilities.
How can you tell? Your solution provider should be aware of all risks, especially cybersecurity risks. They should know how to quantify breaches (in terms of legal vulnerability, revenue losses, missing deadlines, material waste, data leakage and so forth). No less important, they should know how to deal with issues in real time.
Check what steps they take to maintain security:
- Is their system architecture resilient?
- Do they use encryption? What kind?
- Do they have some kind of access control?
- Do they use authentication and authorisation?
- Do they have threat detection (threat intelligence)?
- How do they alert?
- What happens in the case of a breach?
- How can they support you in regards to team training (understand what their service does and does not include)?
- Build a detailed security flow and project plan –
You may ask a 3rd party consultant or use your IIoT vendor to structure a methodic security plan. It must include rules about who is allowed to access the data (user roles), what data is accessible by anyone on the team, what periodical reports should be generated, etc.
Map all your digital assets so it would be easy to locate any breach and handle it. Have a security team on board and security gateways in order. Again, consult your IIoT SAAS partner to better understand how this is optimally done.
- Train your employees and partners –
A lot has been said about cyber-security training programs. There’s so much to say about it that I just can’t add it here. Again, leverage your IIoT software provider to onboard a successful and comprehensive security team training. Plataine, for instance, can share a lot about this type of training such as what training is best carried out in steps, how, what guidelines to share, etc. I am sure that other vendors can provide such support as well, you just need to ask. by the way, don’t forget to include ongoing simulations periodically. Nothing works better than that.
Each one of your employees should be educated on procedure to prevent cybersecurity risks.
- Understand it never ends –
Keep monitoring your security status and consider additional security measurements to take. Always be on the lookout for possible threats. We share news with our customers, and I guess my best advice for anyone in this business is to proactively look for news and learn from “new versions” of related attacks (or attempts) that were experienced by similar industry players.
- Have a crisis plan for an attack –
Simulate that an attack occurred and plan for immediate reaction and for the day after in terms of response and recovery. What measures will you take to contain the damage? Make sure you can restore your data. Hire the right people to handle such a crisis or have a partner you can talk to in case of a breach suspicion. Don’t forget to plan what your post-attack analysis will look like.
- Use an external source to assess your security project plan –
You’ve prepared well? That’s great. Let someone else, an expert, an outsider, see and asses your entire documentation, charts, flows, etc. In other words, get another opinion. This will ensure you didn’t miss anything critical.
For further explanation on best practices regarding cyber security and Industry 4.0 check out the NIST Cybersecurity Framework.
Summary
New technology carries new risks. This is usually the case with any technology. The connected factory and IIoT in manufacturing is no different.
Indeed, for discrete manufacturers a security breach may be extremely harmful.
But, risks and threats are by no means showstoppers, at least not if manufacturers wish to survive and flourish in this ever competitive arena. And the only way to do that is to gain the needed knowledge, plan ahead and work with the right IIoT partner, one that uses advanced cyber security technologies and knows how to avoid risks and how to minimize the losses in case of a breach, if one occurs.